Or E2EE is fundamentally the most important, privacy-vise, a mechanism for making communications as secure as possible. Before we dive in, let first draw a diagram explaining how the non-E2EE systems function:
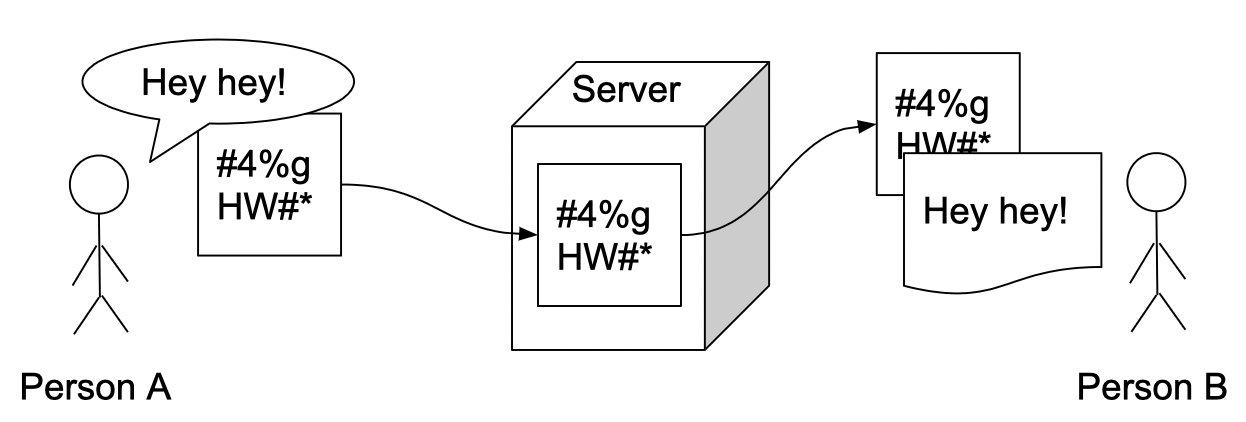
As you can see, we are communicating with each other by encrypting messages between us and the mail server (for example, it can be any other server type design for information sharing) in order to ensure secure communication between us. Then the server initiates a second encryption branch between itself and the person or entity, virtually on our other end. But, as you can see on our other end is not person B but, rather, it's the server providing this service. We are not saying these vendors are going into your content but, we are definitely saying they could if they wanted to.
Now let’s check out the nutshell of E2EE:
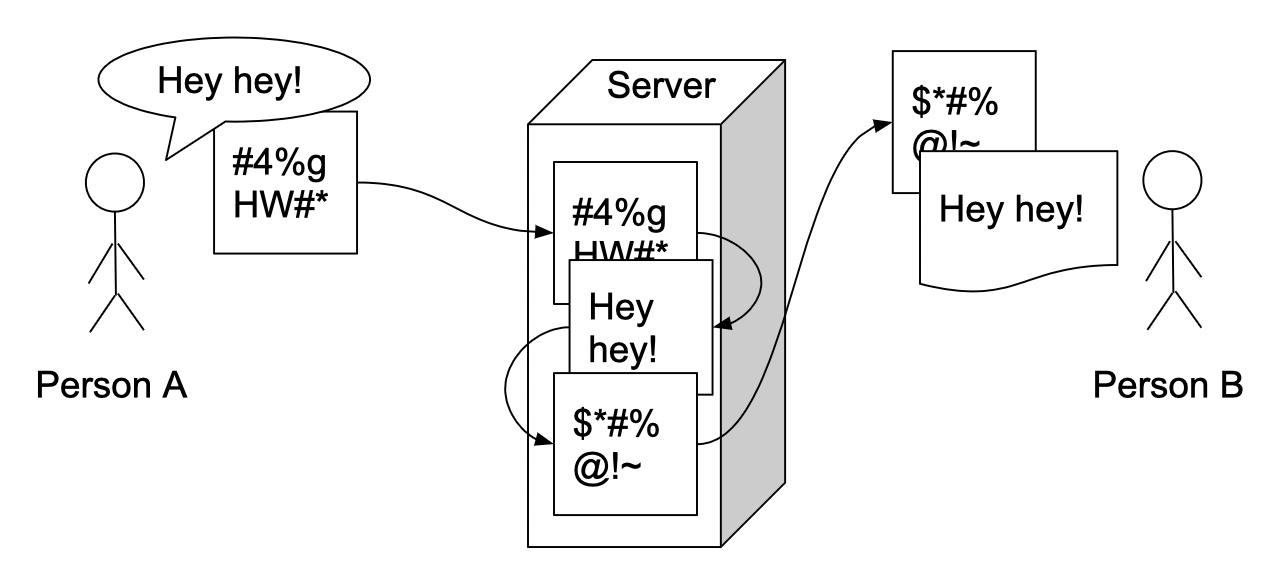
In the graph above you can see that messages are going through the server allowing remote communication, but it is not doing any funky decryption/encryption process. It is simply due to the fact that it is not capable of such a thing. We have persons A and B who are encrypting their messages with each other's keys and not using the server for anything other than a simple proxy. We need it just to store encrypted messages for persons with appropriate keys to read them, no decryption is being performed on this level of communication.
Encryption keys
Encryption can be performed via symmetric or asymmetric algorithms. Asymmetric algorithms (RSA for example) are interesting and clever systems with a lot of math in order to generate something called public/private key pairs. Private keys are used to decrypt messages received by someone who used our public key to encrypt the message for us. Check out this page: https://bluegrid.io/edu/how-asymmetric-encryption-works/.
For symmetric encryption, we need to have the mechanism to share the keys we’ll be using to encrypt our messages. Usually, what’s being used is the Diffie-Helman protocol which is a pretty clever way of sharing the secret via remote communication channels. Why? Because if we shared our encryption keys over insecure channels it’d be the same as communicating without encryption whatsoever. How it works:
- Persons A and B agree to use the modulus of prime number p and base g (g is primitive root modulo p)
- Person A generates integer a and sends it to
- Person B (message A = g^a mod p)
- Person B does the same (message B = g^b mod p)
- Person A does some math: key = B^a mod p
- Person B as well: key = A^b mod p
The key is the same and both parties can use it to encrypt their messages. You can use different online tools to play around with different values and see how this math works in practice: https://www.irongeek.com/diffie-hellman.php.
Subscribe to be updated on the new content!

